@warkwarth Tell your friend they use a serious series of algorithms to crawl the internet using the search term “youremailaddress.”
Mind you I haven’t used the app in 14 years, so I don’t recognize it anymore.
Example of Maltego in action
I’m still bored so, here’s an (as brief as I can make it) idea of how security worked in the 2000’s.
Everything on the internet uses “ports”. (Your PC does too.) port 80 if for web browsing, 443 is for secure browsing. http:// vs https://. Ports 587, 465 and a bunch more depending on the service being provided. (Web mail, company server’s like Exchange…) Pretty complicated actually. Online games use ports. Can you access your company from home (work from home)? Another port. Note that there is a default port for that which should be changed because every hacker knows what ports are used.
Your modem/router/wifi has a LAME ass firewall. Businesses should be using a real firewall. (My description here will be out dated, but you’ll get a rough idea.) A real firewall blocks ALL ports until they’re opened. If you want to have a mail server you must open those ports. It examines the actual packets of a conversation. (More details below.)
All computers have a numerical internet protocol address. IP address. Again, I’ll talk about IP v.4, not v.6 to keep it simple. There are public and private addresses. One simply CANNOT talk to the other. It’s written into the protocol. Microsoft’s “public” address is: 13.107.246.59. I have no way of finding their private ip’s. Private ip’s will be something like 192.168.1.1, or 10.10.10.1
Man, I’m having a devil of a time keeping this down to less that 100 pages!
Data sent between computers are in the form of “packets” containing routing (Think post office) and the payload, data. Pictures, videos, email… Kinda…
Not relevant to hacking as far as this article goes, but just interesting. On November 25th, 2019, the world ran out of IPv4 addresses. IPv6 was implemented on July 14th 2017. Close call, eh?
IPv4 allows for 4,162,314,256 addresses. These are “public” addresses only. Not those private addresses used inside homes and offices. They are 8 bit. 1.1.1.1.1.1.1.1 X 4 octets. All those 1 add up to a computer, to 255. But only 254 can be used. Why? If you wanna know, I’ll explain, but it’s another book. Hence 254254254*254 = that 4+ billion.
IPV6 uses 128 bit resulting in an 340 undecillion! Have you ever even heard of that? Not me. We should know by the end of the decade. I’m sure the US will be at least in 1 undecillion in debt.
An undecillion contains 1000 billion billion. Hada ask google.
Okay, back to killing time.
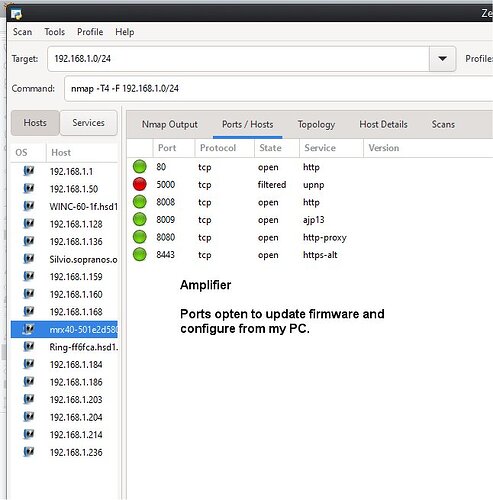
There’s an app called zennmap. Enter the addresses of a business, and it scans to see what ports are open on the entire network. There’s a way to enter a bunch of addresses in a “group” but then we’d have to get into sub-netting and that’s another book.
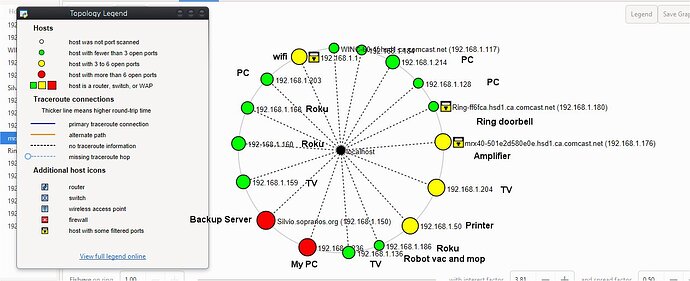
It’ll also produce a diagram, like this one of my home network.
Here’s what it found open on my amplifier:
But wait, there’s more! WAY cooler!
Remember I mentioned a “real” firewall? They do something called stateful packet inspection. Not just blocking ports. They open a packet, see where the request came from, what was requested, it see’s the request to send, the acknowledgement that it received the request, a response and a TON of other shit.
Wifi routers do too but not the extent. Well, maybe they do now… I just know that when I go into my router, the “firewall” is set to low. Set it to at least medium. I tried setting it to high, but my ring doorbells and thermostats didn’t work. Until I opened the ports.
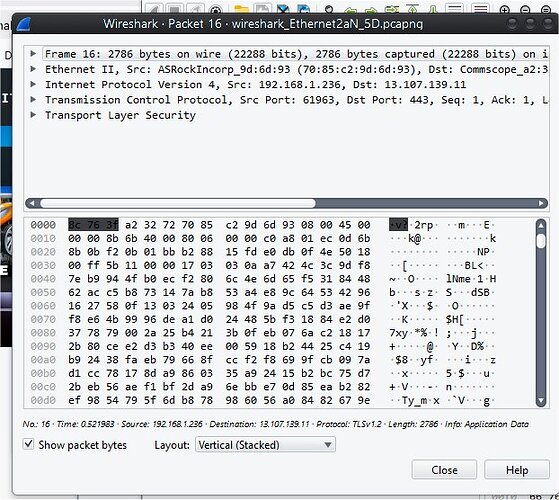
There’s an app called Wireshark. It can open and read packets too. Here’s an example of what ONE packet looks like and how much info a packet inspector has to examine before allowing or denying. The top is “Supposed to be” human readable, the bottom is what a computer see’s. Kinda.
This is 10 seconds. 1,130 packets. Fast, eh?
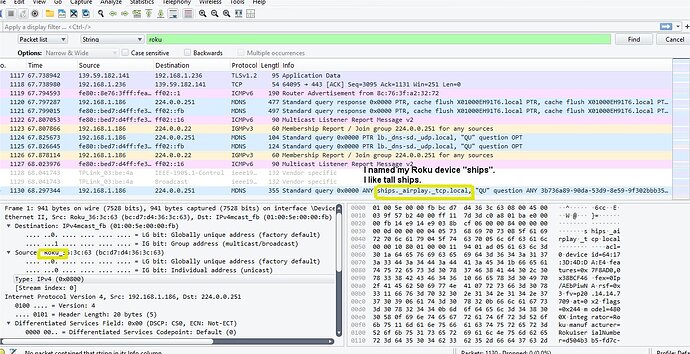
Here I can see my wife is watching TV via Roku. Probably Bobby Flay on the food channel. I think she has a crush on him. That’s all I ever see.
There are dozens of apps that’ll now do all this for you. Plus they can see what versions of security protocols, recommend you upgrade them, warn you of vulnerabilities, what to do about them and a LOT more.
Here’s an example of an exploited vulnerability
© SANS Institute 2000 - 2005 Author retains full rights. (Where I got my training) Here is an explanation of the SSH1 Man-in-the-Middle attack to show the ingenuity of the
programmers. First one must poison the cache to have the traffic routed through the attacker’s
machine. Once the client requests an SSH1 session from the server, the attacker intercepts the
key generated by the host and forwards its own key to the client. The client, thinking they are
communicating with the secure server, now sends authentication and session information to the
server.
The attacker decrypts this information and encrypts it using the server’s original key and
passes it to the server. Once in the middle, the attacker has access to all traffic. It’s easy to see
that this software can be used anywhere on the LAN.
Well, there’s a 1 undecillion mile overview.
Let’s see, I started writing this at about 10:30 am, went to see an orthopedic surgeon between 2:00 and 3:30. continues the, put food on the oven at 6:00 pm, and at 7:00 pm I continued. Now, at 7:13 pm. I’m done!
I don’t care if you read it. I just killed some time!!!